 Blog
Blog
Announcing Layered Network Intelligence for AWS
Defend Your Cloud Without Friction
Ryan Davis
March 23, 2022
Cloud environments are notorious for visibility gaps that weaken security. Unmanaged workloads, serverless environments, and containers that only exist for minutes all combine to create even more blind spots. While agents and perimeter-focused solutions have their place in a cloud security toolset, they also have serious limitations. Perimeter-based security controls can't keep out all the constantly evolving advanced threats that attackers throw at them, and adding agents to workloads requires buy-in from DevOps, which can be a major point of friction for security teams. Plus, it's impossible to deploy an agent on every asset you need to secure.
To truly defend cloud environments from advanced threats, organizations need to take a layered approach to security. With the latest technical innovation for Reveal(x) 360, they can do just that.
Reveal(x) 360 now offers continuous visibility based on VPC Flow Logs for securing AWS environments. Organizations can choose flow logs as a standalone option or combine that cloud-native data source with packets to take a multi-layered approach to cloud threat defense.
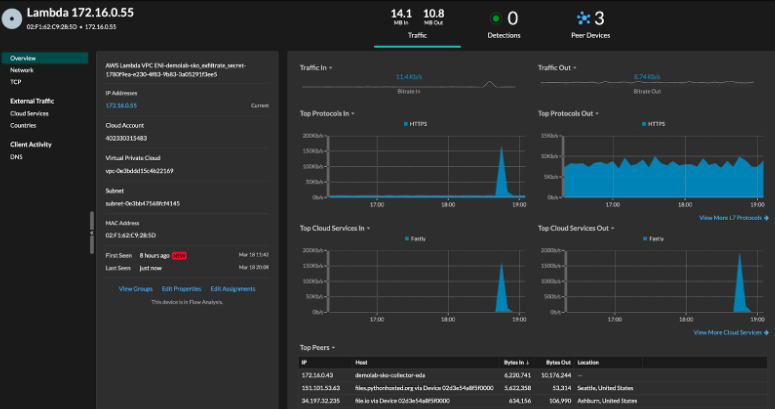
Lambda function visibility in AWS unlocked by VPC Flow Logs and available in the Reveal(x) 360 management pane.
The ability to access multiple data sources in the same management pane will be a game-changer for security teams. First, it significantly reduces blind spots with complete and continuous visibility across workloads by combining the breadth of VPC Flow Logs with the depth of network packets. It also offers more coverage by analyzing multiple sources of network telemetry to detect advanced threats like ransomware or software supply chain attacks. Additionally, this multi-layered approach enhances ExtraHop's already formidable device discovery, threat hunting, and investigation capabilities.
Reveal(x) 360 cloud threat defense offers:
Multi-Layered Analysis and Threat Detection
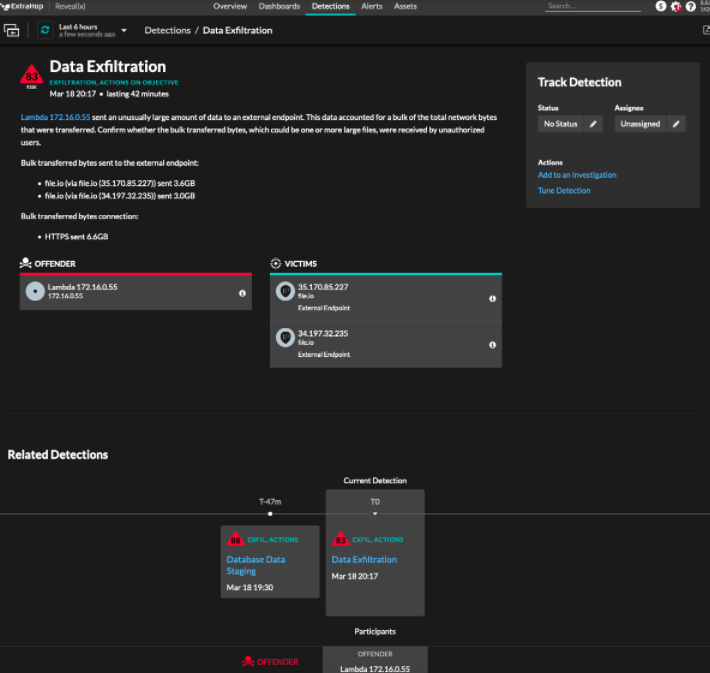
Data exfiltration attempt in AWS leveraging a Lambda function detected by Reveal(x) 360 using VPC Flow Logs
VPC Flow Logs are popular for cloud security because of their value for compliance, but for many organizations, the value stops there. Or, more precisely, it ends with VPC Flow Logs gathering dust in an S3 bucket. That's a missed opportunity. Reveal(x) 360 analyzes all forms of network telemetry with advanced AI for comprehensive behavior monitoring across IaaS and PaaS workloads, as well as containers and serverless deployments. What it means for the end user is simple: You can use ExtraHop's real-time analysis and data visualizations to improve your situational awareness, gain actionable intelligence, and quickly zero in on malicious activity. Additionally, adding VPC Flow Logs to Reveal(x) 360 enhances threat detection capabilities for post-compromise techniques like command and control and data exfiltration.
Breadth and Depth of Visibility
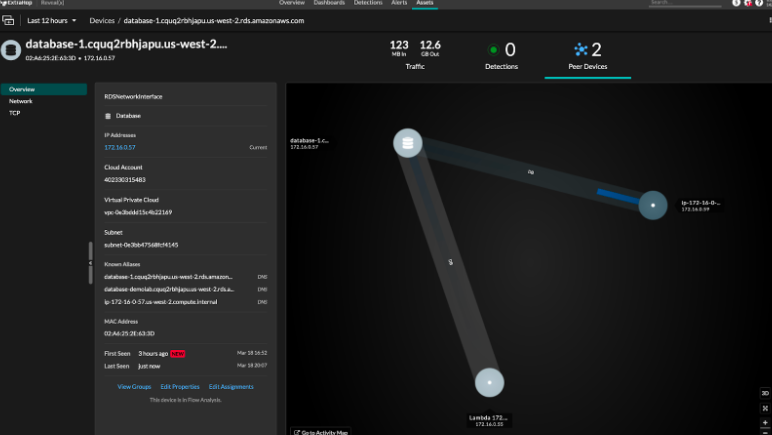
Amazon Relational Database Service (RDS) visibility in the Reveal(x) 360 management pane via VPC Flow Logs or packet visibility via VPC Traffic Mirroring.
With the ability to combine VPC Flow Logs with packets in a single platform, Reveal(x) 360 doesn't force you to choose between coverage that's a mile wide and an inch deep or very deep but limited in breadth. This complete and continuous coverage enables security teams to quickly identify and investigate post-compromise behavior like lateral movement as a way to stop attacks before they become breaches. Analysts can use VPC Flow Logs for broad coverage and packets for deeper visibility and investigation. Organizations that need Amazon Relational Database Service (RDS) monitoring can use VPC Flow Logs or gain packet packet-level visibility with VPC Traffic Mirroring.
Frictionless Cloud Threat Defense
Reveal(x) 360 deploys without agents and provides out-of-band analysis of network telemetry, eliminating a major source of DevOps friction and freeing security teams to do their jobs without slowing down innovation, digital transformation, or business. Layered cloud threat defense also helps reduce tool sprawl and complexity. In the past, gaining access to multiple data sources often required using multiple products and user interfaces. By ingesting VPC Flow Logs and packets, Reveal(x) 360 enables analysts, forensic investigators, and incident responders to access layered network telemetry in a single management pane for unified threat visibility, investigation, and response.
Reveal(x) 360 Subscription Tiers
Reveal(x) 360 offers several subscription tiers for multi-layered cloud threat defense in AWS. Every subscription tier leverages ExtraHop's secure, cloud-hosted services, AI analysis, and record store for frictionless visibility and investigation. Organizations can purchase the new Reveal(x) 360 Standard subscription for continuous visibility in AWS powered by VPC Flow Logs, or they can combine their subscription with Reveal(x) 360 Premium or Ultra packages for deeper visibility, expanded detections, and enhanced investigation. To view Reveal(x) 360 subscription tiers, visit our AWS Marketplace listing.