 Blog
Blog
Faster Threat Response with ExtraHop + Cisco ISE
Cut time between breach detection & containment
Christine Shaw
April 23, 2019
When it comes to security incident response, responding quickly is key. Whether it's ransomware, data exfiltration, or command and control activity, the quicker a threat is detected and contained, the better your chance of minimizing damage.
The ExtraHop Reveal(x) integration with Cisco Identity Services Engine (ISE) helps minimize the time between discovering a breach and containing it by combining ExtraHop's anomaly detection with ISE's endpoint-based network access and policy enforcement capabilities. Check out this short video to get a feel for the integration, or keep scrolling for technical details and how to get started:
How It Works + Why It's Valuable + How To Get Started
How It Works:
The integration utilizes ISE's Adaptive Network Control (ANC) service, which can be used to modify an endpoint's network access through the admin UI or third party systems. To quarantine a device from ExtraHop, all you need in ISE is an ANC policy with an action set to QUARANTINE and a corresponding exception policy.
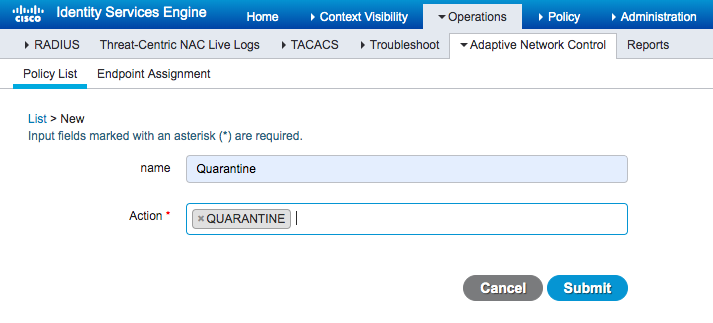
ANC policy creation
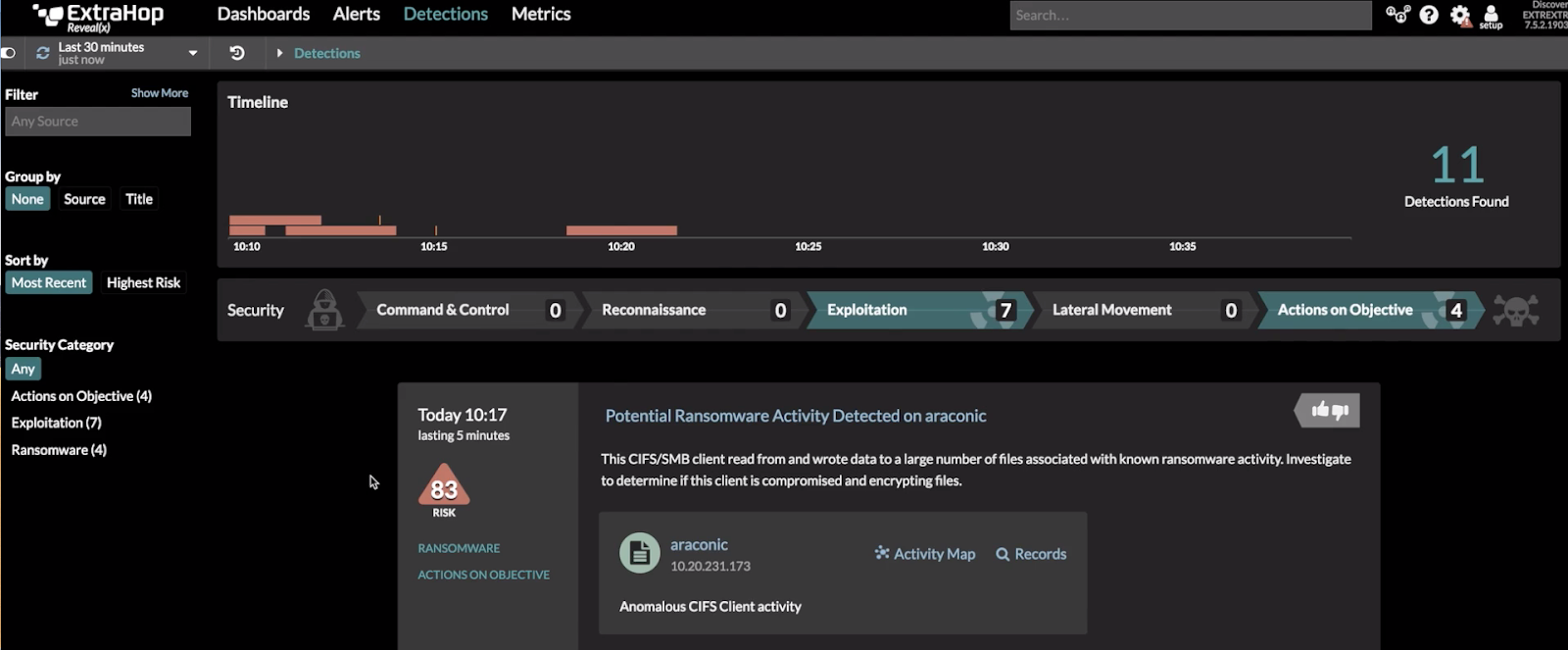
ExtraHop's behavior- and rule-based anomaly detection catches suspicious activity and potential security threats as they happen. When a high-risk detection or alert occurs, an ExtraHop trigger sends a request via Open Data Stream that assigns the device to the ISE quarantine policy.
Why It's Valuable:
The ISE new supported bundle makes it easier for joint ExtraHop + Cisco Customers to have automated detection for threats like ransomware and data exfiltration where anomaly detection and quarantine response happens instantaneously as the data comes over the wire. Security threats are immediately quarantined and can be investigated further by SOC teams using ExtraHop Detections in the Reveal(x) User Interface.
How To Get Started:
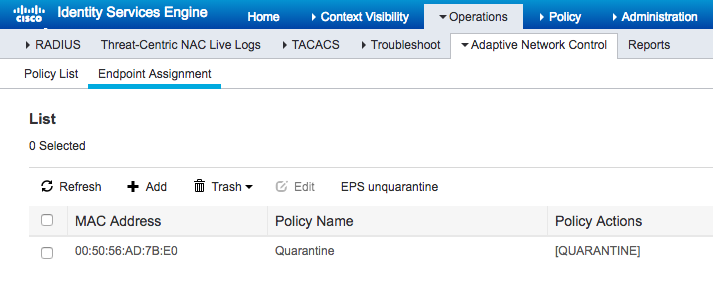
Quarantined device in ISE
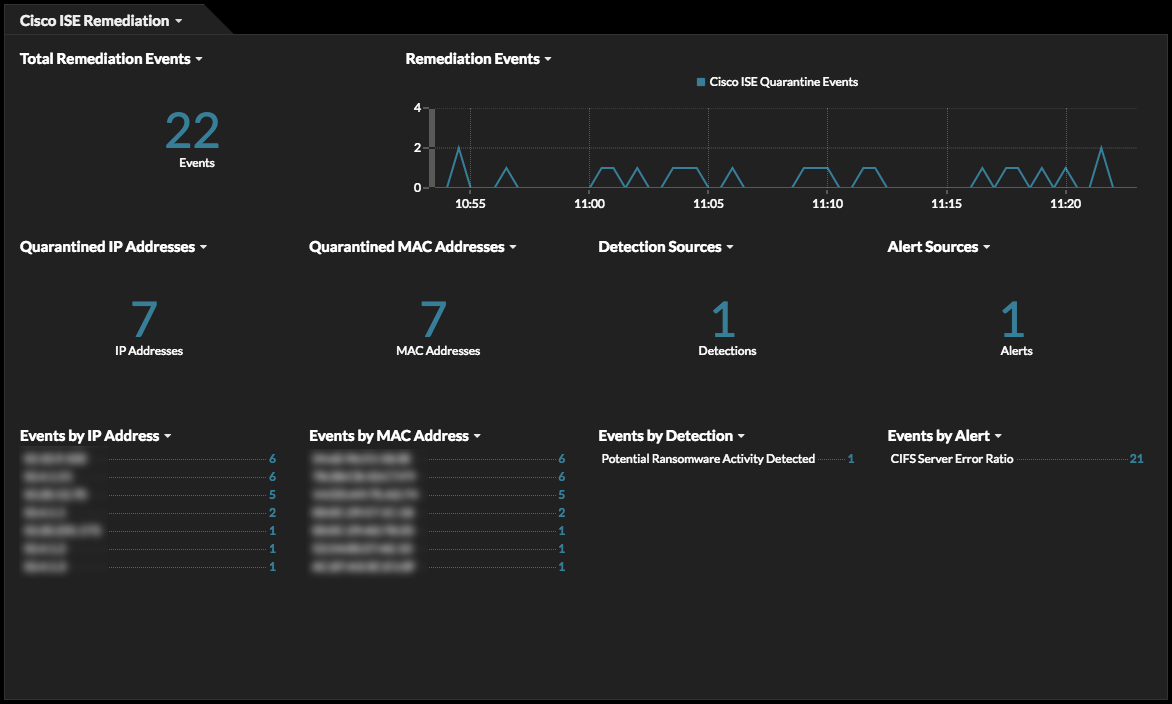
Setting up the integration in ExtraHop requires a few simple steps that are detailed on the bundle gallery page. The bundle includes two triggers that extract device IP addresses or MAC addresses from specific detections or alerts and then sends them to ISE, as well as a dashboard to show the overall status of the integration.
Download the datasheet detailing ExtraHop Reveal(x) + Cisco ISE here.
Meanwhile, scroll down for more on network traffic analysis, proactive security postures, and the latest Reveal(x) features!
Discover more