 Blog
Blog
ExtraHop Reveal(x) + CrowdStrike Integration: How It Works
Combine NDR and EDR for fast, confident threat response
Jesse Munos
June 3, 2020
In the world of Network Detection and Response, many vendors forgo the Response capabilities entirely while other vendors have latched onto complicated and potentially dangerous approaches. For example, some vendors rely on alert-based triage notifying analysts to investigate potentially malicious traffic. This approach can allow malicious code access to systems for hours or days while analysts work through a backlog of alerts. Other approaches use a crafted form of denial of service, which increases network overhead and may have unintended collateral consequences such as increased network latency, dropped legitimate packets, and general network congestion.
Rather than follow these subpar approaches, ExtraHop leads by partnering with other best-of-breed security vendors such as CrowdStrike to provide specific endpoint-centric response capabilities. When integrated with CrowdStrike, Reveal(x) enables you to take customizable automation action directly on an endpoint without the potential risks associated with alternative forms of response actions. ExtraHop is able to detect and respond to network based malicious activity in seconds by leveraging CrowdStrike's network containment capabilities—preventing small problems from growing into large ones and reducing the Mean Time To Detection.
How Does It Work?
Reveal(x) monitors and analyzes all network traffic for potentially malicious activity by extracting more than 5000 traffic features our cloud-scale Machine Learning uses to detect anomalous behaviors. When a detection occurs, a trigger is fired which evaluates the detection for response by CrowdStrike. If the detection risk value meets or exceeds the trigger threshold, Reveal(x) sends a request to CrowdStrike to begin network containment of the offending endpoint.
Dashboards and Data
The CrowdStrike Containment dashboard provides several key pieces of information such as the number of qualifying detections, how many and which hosts are currently contained, the IP addresses of those hosts, and errors around any detections that did not have valid CrowdStrike Sensors.
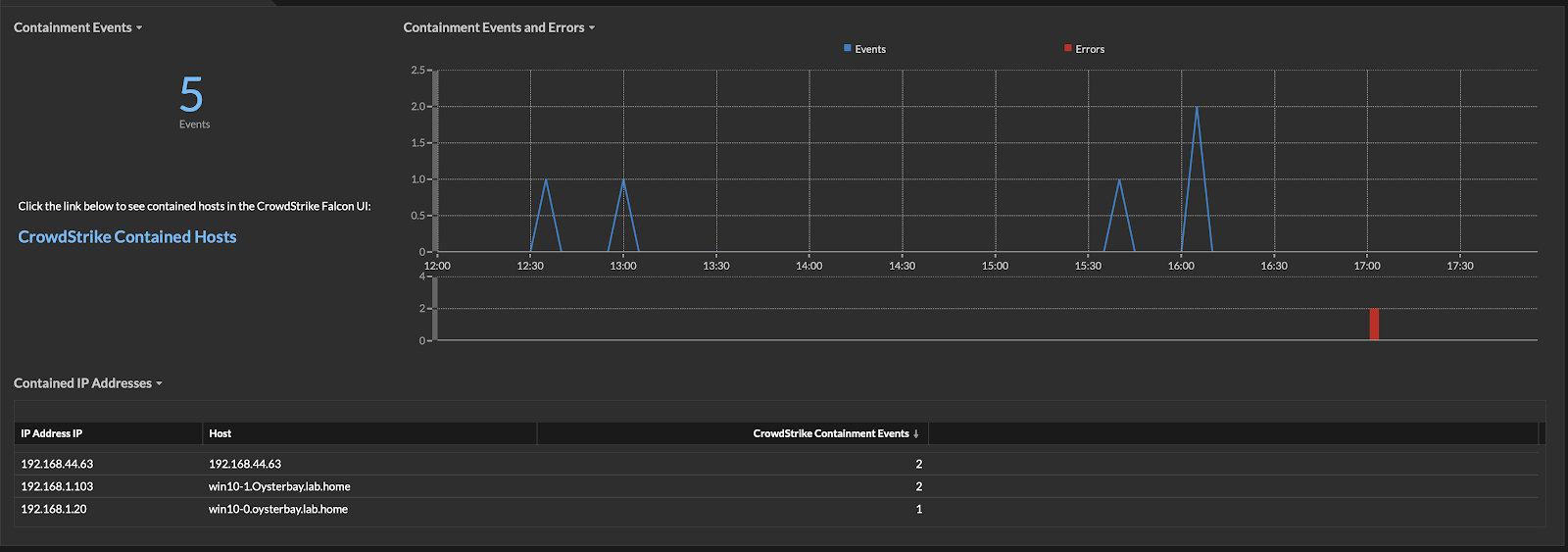
Additionally, by digging into the record data in the dashboard, you can find even more information to assist with any investigation. Record data includes the offender endpoint's MAC address and the title of the detection which triggered the behavior. If the detecting Reveal(x) appliance is set up to store raw packets, there will also be a link to access the packet data!
Configurable Options
The CrowdStrike Network Containment Trigger has three configuration options that you should know about:
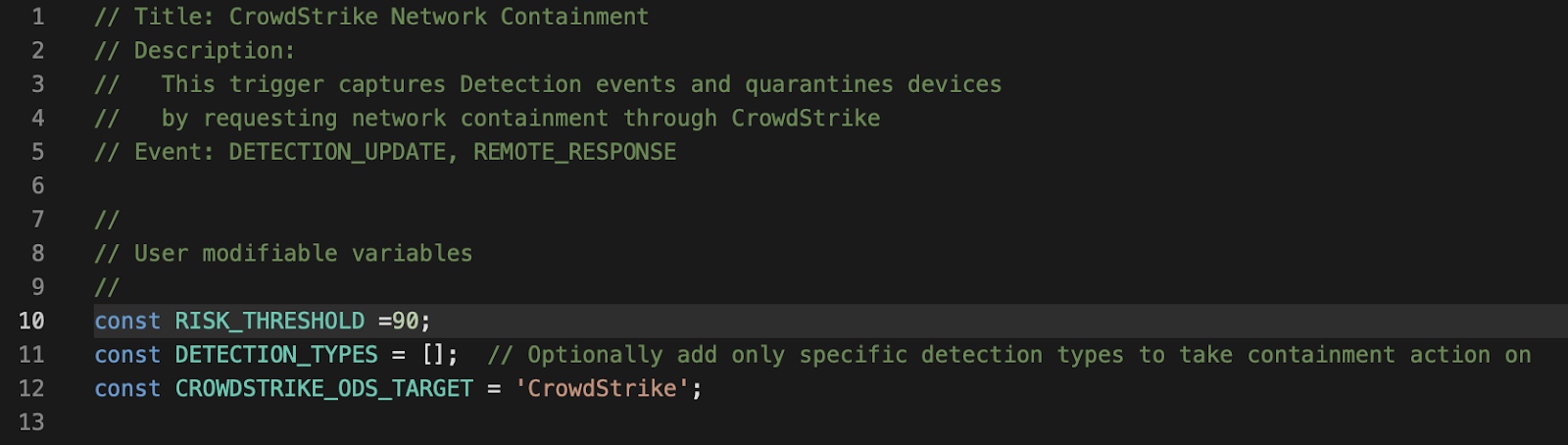
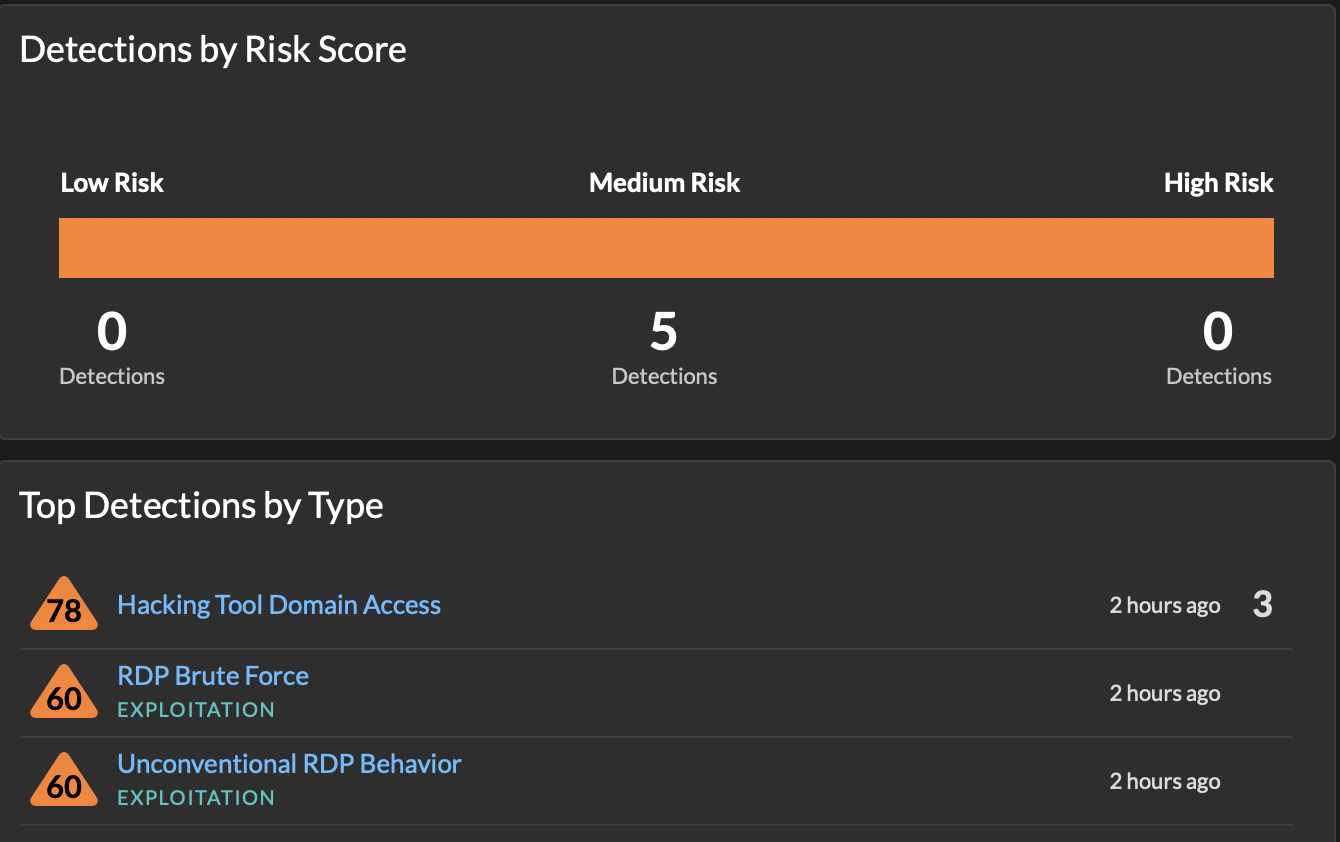
The first option is the RISK_THRESHOLD. The RISK_THRESHOLD for a given detection is determined by looking at the Risk Score available from your Overview or Detections dashboards. Depending on the types of alerts typically seen in an environment, the RISK_THRESHOLD should be tuned to prevent non-critical alerts from triggering the network containment feature.
The second option is the DETECTION_TYPES. This array allows users to specify custom-built detections that will request endpoint containment. Custom detections are a very powerful tool, allowing analysts to design and deploy detections based on a wide variety of parameters. For more information on Custom Detections, click here.
Finally, the third option is the CROWDSTRIKE_ODS_TARGET. This field is less of a customization option than it is the critical link between the CrowdStrike ODS mechanism and ExtraHop detections. You can customize this field with any name so long as it exactly matches (upper case, lower case, punctuation, etc.) the name of the ODS target created during the integration setup process.
If you would like more information on setting up the CrowdStrike integration, please see the CrowdStrike Network Containment Integration guide.
Discover more