Monitoring Encrypted SSL/TLS Traffic
The new standards TLS 1.2 and 1.3 utilize perfect forward secrecy (using Elliptic Curve Diffie-Hellman Encryption), which creates an ephemeral session key. The ephemeral secret is only used for that conversation, and cannot be derived from the private key of either the server or the client. For hackers trying to steal large databases of intellectual property or millions of credit card numbers, this presents a significant challenge. Unfortunately, the same challenge is presented to SecOps teams who need visibility into their traffic in order to detect and investigate threats.
As of 2021 98% of web traffic loaded by Chrome occurs over HTTPS connections secured with SSL/TLS. TLS is the modern successor to the deprecated SSL protocol—this is commonly referred to as SSL/TLS. Security best practices advise teams to utilize TLS 1.2 and 1.3 with perfect forward secrecy to secure web traffic and ensure the confidentiality and integrity of data in transit.
Decryption with ExtraHop Reveal(x)
See into Encrypted Active Directory Protocols
Automatically discover and classify all devices communicating on your network—including those using encrypted Microsoft protocols. Protect your sensitive data while maintaining compliance with various industry standards such as HIPAA, PCI, GDPR, and others.
Monitor Encrypted SSL/TLS
Detect suspicious behavior across all on-premises and cloud assets. Unlike tools that stop at TLS fingerprinting or use a method similar to signature-based detection called encrypted traffic analysis, SSL/TLS decryption allows the application of behavioral analysis and machine learning to all network traffic in flight.
Get Intelligent Integrations
Automate investigation workflows by connecting detections from Reveal(x) with tools like CrowdStrike Falcon and cloud services. Take advantage of robust integrations and cut your overall time to resolve threats 84% faster.

Without ExtraHop, the investigation would have taken days or weeks … Even the FBI was impressed when they found out how quickly we identified and contained the threat!
Joanne White
CIO,
Wood County Hospital
Critical Insights Without Compromising Privacy
The advent of advanced encryption adds new ways for attackers to avoid detection—yet avoiding encryption is not an option for organizations who want to thrive in the modern digital era. ExtraHop Reveal(x) is the only NDR product capable of decrypting SSL/TLS with perfect forward secrecy and Microsoft Active Directory protocols at line rate, and without putting any sensitive data at risk during the process.
As discussed in the 2021 SANS SOC Survey, "In our follow-on questioning, we heard that the most common reason for not using TLS intercept is corporate concern over regulations and privacy. However, no one using TLS intercept reported running into legal issues. One respondent pointed out the need for management education in this area."
Ready to Learn How It Works?
Meet ExtraHop Reveal(x)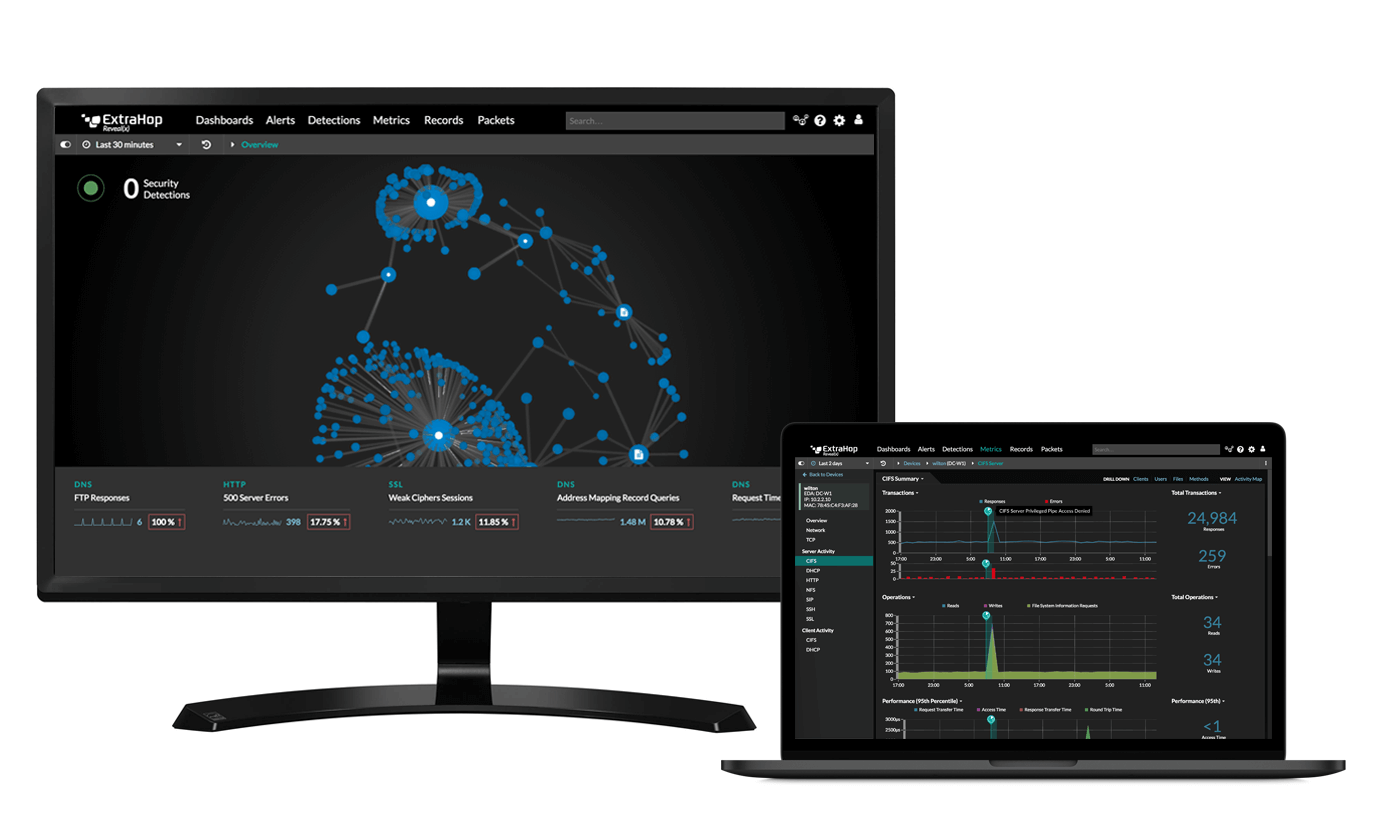
Start the Demo
Stop data exfiltration, insider threats, and more with the full product demo.
Start Demo
