 Blog
Blog
Security Alert: New Vulnerability Grants IoT Camera Remote Access
ThroughTek CVE-2021-28372
Jeff Costlow
August 19, 2021
On Tuesday, August 17, a joint disclosure by Mandiant, the Cybersecurity and Infrastructure Security Agency (CISA), and ThroughTek revealed that a critical vulnerability (CVE-2021-28372) may allow attackers to access millions of IoT cameras, allowing them to view and record live feeds and compromise credentials for further attacks.
The vulnerability affects devices that use the Kalay protocol built with the ThroughTek Kalay Software Development Kit (SDK), which is used by numerous device manufacturers providing an estimated total of 83 million recording devices, ranging from enterprise security cameras to smart baby monitors.
Products built with the ThroughTek SDK and using the Kalay protocol are vulnerable to improper access controls, meaning an attacker could identify and register devices on the Kalay network, granting them access to sensitive information such as real-time audio and video feeds and enabling remote code execution which essentially gives them full access to an organization's network.
Impact and Mitigations
ThroughTek has released a patch for the vulnerability, and IoT manufacturers that use the Kalay protocol should upgrade to the latest version immediately. End users should avoid accessing their ThroughTek devices on untrusted networks until software updates have been released and installed on any impacted device.
Vendors using the ThroughTek SDK should take mitigation steps including updating to ThroughTek SDK v3.1.10 and above as well as enabling two Kalay features: Datagram Transport Layer Security, which protects data in transit, and AuthKey, which adds an additional layer of authentication during client connection. CISA also recommends minimizing network exposure by isolating any potentially impacted devices behind firewalls and separating them from business networks.
Identifying devices using the ThroughTek Kalay services can be difficult. Many original equipment manufacturers (OEMs) use the service without telling the customer. ExtraHop has added device identification in Reveal(x) for any device that uses the afflicted Kalay protocol. In addition to checking for affected devices and regularly updating software, we recommend that affected organizations stay vigilant for any post-compromise activity.
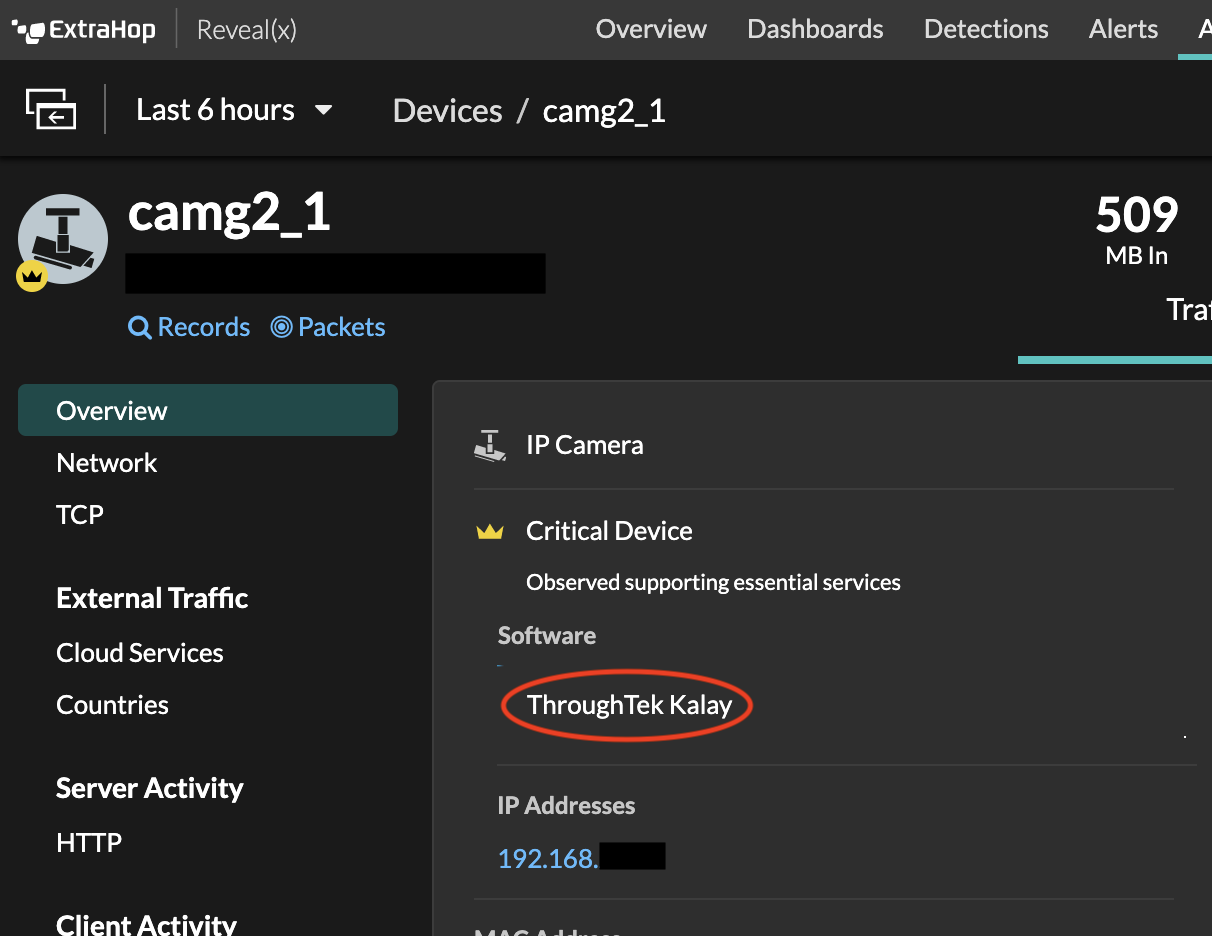
Affected Devices will have software identified as "ThroughTek Kalay."
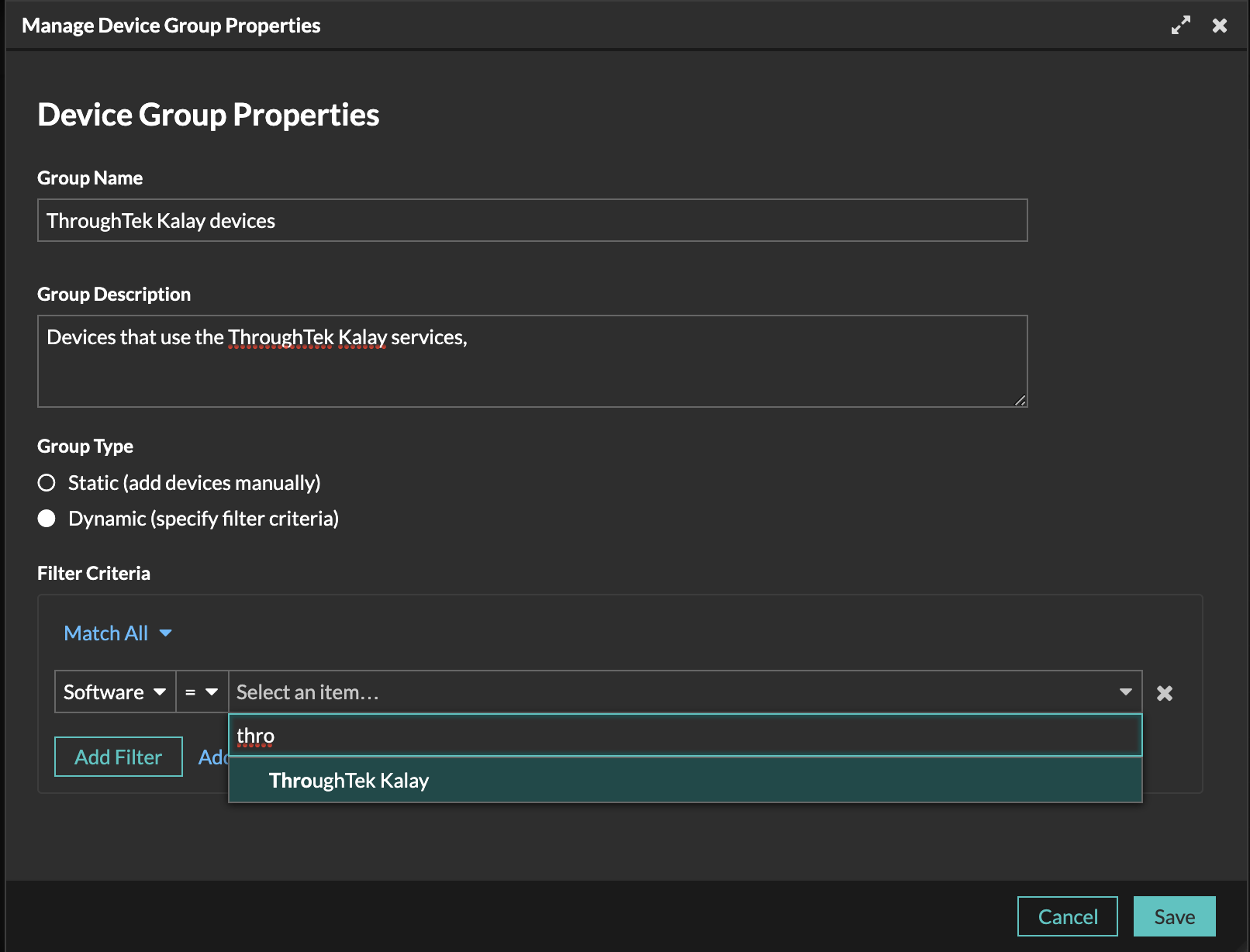
Reveal(x) customers can create a device group to find all devices.
ExtraHop is preparing to publish a Threat Briefing for this issue which will automatically identify all the devices using this service.
The Challenges of Securing IoT
Because the affected ThroughTek SDK and Kalay protocol are used by many IoT manufacturers, affected devices may be found in a wide range of environments, including compliance-focused industries such as healthcare. This vulnerability highlights the increasing challenges of supply-chain security, which often demands immediate action by the software supplier, the manufacturer, and the end user to release patches and apply necessary software updates. As mentioned above, devices using these services are often hard to identify because manufacturers may not mention the services. ExtraHop has determined that approximately 1% of our customers have devices that use the ThroughTek Kalay services.
There was probably no clearer illustration of the complexity of IoT supply chain security challenges than the Ripple20 vulnerabilities that were announced by the threat research team JSOF in June 2020. The Ripple20 vulnerabilities were found in a Trek networking stack that had been used in everything from printers and VoIP devices to specialty medical equipment for over two decades. Affected devices were as diverse as they were widespread, affecting an estimated 35% of environments. Tracking down vendors and alerting affected end users proved to be an extremely complicated undertaking.
Adding to enterprise IoT security challenges is the fact that companies are struggling to track and secure the growing number of connected devices. According to ExtraHop data, after organizations switched en-masse to a work-from-home model, the number of connected IP phones declined by just 7.5% and printer connectivity declined by just 0.53%. These figures are especially concerning considering that nearly 25% of those VoIP devices are Cisco IP phones, for which a critical vulnerability (CVE-2020-3161) exists, and that printers are notorious for being a target of hackers.
A key challenge lies in the ability of teams to create and maintain a device inventory. To patch and secure IoT, first you have to know it's there. Further, in many cases, security teams are at the mercy of individual employees to install updates themselves, and many, if not most, lack the technical skills required to do this. This can lead to critical updates that may not be applied properly or in a timely manner, leaving network resources exposed.
Disconnecting these devices when they are not in use is a crucial way for enterprises to reduce their attack surface, but organizations can further protect themselves by implementing proper network segmentation, Zero Trust security policies, and deploying security tools that can offer both IoT visibility and detect threats post compromise.
Discover more