 Blog
Blog
Most Security Pros Wish Their Company Did More Threat Hunting. Here's How They Can.
Plus, we'll provide some clarity on what threat hunting actually *is*
Chase Snyder
April 22, 2020
Cybersecurity Insiders just released the results of their survey about threat hunting practices. The results confirm that security professionals generally think threat hunting is a good idea and wish their organizations would be doing more proactive threat hunting than they are. Fair enough.
The results also highlighted a divide, or lack of clarity, in the definition of the term "threat hunting" itself. In the Cyber Security Insiders survey, 52% of respondents indicated that their threat hunting efforts were primarily proactive (commencing before any threat is detected) and 48% indicated a reactive approach (in response to a new or ongoing incident).
Moreover, 59% of respondents indicated Automatic Threat Detection as the most important feature for a threat hunting tool. This indicates that the respondent pool has a widely ranging view of what kind of activity can be considered "threat hunting" versus investigation, incident response, and other related activities.
What Do the Other Experts Say?
Everywhere you look, you'll find slightly different definitions of threat hunting, but in general there's broad agreement that it is a proactive process.
A SANS research paper on the topic focused on manual, analyst-driven approaches:
"The formal practice of threat hunting seeks to uncover the presence of attacker tactics, techniques, and procedures (TTP) within an environment not already discovered by existing detection technologies...threat hunting [is] the proactive, analyst-driven process to search for attacker TTP within an environment."
A recent ISC(2) blog post included more preparation-focused, detection oriented methods, including setting up honeypots and "salting production databases with watermarked data" to lure criminals and trace criminals.They advocate a broad conceptualization of threat hunting:
"...threat hunting inputs run the gamut—from eavesdropped conversations among criminal gangs to analyses of server logs and user behavior. Some threats are malicious, while others are not. An organization's concept of threat hunting should encompass this whole scope, even if its coverage is limited."
Basically every vendor in the enterprise security space has some blog post or other publication on the topic of threat hunting that starts out with a nod to "proactivity" but then goes on to describe a range of differing priorities. So far, standardization in threat hunting has only progressed to the form of a relatively simple, though widely adopted, prescriptive model, created by David Bianco (see below). While this model has driven tons of progress, compared to the more complex, robust and formalized standards in other realms of security such as incident response and forensics, threat hunting has a long way to go.
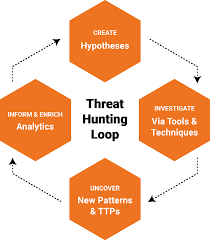
Security Teams Building Threat Hunting Programs Have An Opportunity
Sixty-five percent of respondents to the Cybersecurity Insiders survey said that they were planning to build a threat hunting program in the next three years. For security teams looking for guidance on how to build out a threat hunting program, the fuzziness around defining the term may be frustrating, but a better perspective would be to treat it as an opportunity to develop a greater understanding of their own environment and create the threat hunting program that works for them.
As segments in any market become better established, they tend to devolve into lists of mandatory checkboxes that may or may not actually apply to a given company's needs—especially in a space that evolves as rapidly as cybersecurity. Take traditional signature-based IDS/IPS. Many organizations still maintain an IDS/IPS system because at one point they were told it was required, but because the ratio of false positives is so high, security teams ignore the thousands of alerts these systems emit. In other words, having the tool is good optics, but using the tool is more work than it's worth.
The current lack of formalized and regulated definitions in the threat hunting space means that security teams don't have to succumb to checkbox syndrome in this case, and can focus their efforts only on the most value-creating approach to threat hunting for their particular environments, without having to consider externally defined requirements.
Learn From A Pro: How To Build A Value-Centric Threat Hunting Program
In conjunction with this survey, we conducted a webinar to highlight some of the most compelling stats, and to provide concrete, actionable guidance from one of ExtraHop's professional threat hunters, Tanner Payne.
To learn more, watch the webinar and download the final survey report.
Discover more