 Blog
Blog
Show and Tell: What a Live Attack Simulation Looks Like in Reveal(x)
Look over the shoulder of the attacker as they're doing their stuff
Tyson Supasatit
February 12, 2019
"Booth duty" at an enterprise technology trade show can get boring for some people. But not for me! I love being able to demo our product, watching people's reactions as they see what type of information can be gleaned from network traffic. Because people appreciate our demo so much, ExtraHop has put a lot of effort into providing a fully interactive live demo to visitors of our website. With the Reveal(x) Winter 2019 release, we've added a new live attack simulation that allows you to watch as a hacker executes a sophisticated, multi-stage attack.
What makes this attack simulation interesting is that you can see real tactics, techniques, and procedures in action with video captures showing the hacker using tools like Metasploit, Bloodhound, and web shells and employing techniques including PsExec and WSMAN attacks. Alongside the videos, you can track in detail the evidence of the hacker's activities in Reveal(x).
Check out the new live attack simulation
As you watch the simulation, consider what would be the alternative to detect and investigate these activities? Maybe dumpster diving through log files, writing Splunk queries, or grepping through firewall logs? If you were lucky, you'd get some alerts on the attack activity that would give you a starting point for an investigation. Reveal(x) not only surfaces each stage of the attack lifecycle through detections, but also provides ready-made investigation details—everything you need to validate the alert and determine exactly what's going on.
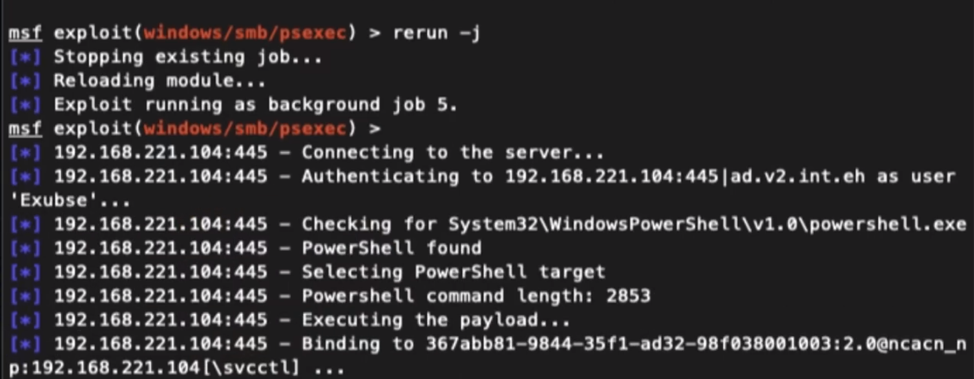
The live attack simulation on Reveal(x)'s online demo includes real tools such as PsExec
Showing Off New Features
The live attack simulation also highlights a number of new features included in the Reveal(x) Winter 2019 release, including:
- Detection drill-downs from detection cards that lead the investigator to specific, narrowed-down details needed to validate an alert, such as servers targeted by Windows Management Instrumentation (WMI) and Web Services Management (WSMAN) requests.
- New detections including for cryptocurrency mining malware and techniques used for lateral movement.
Rising Above the Hype
The enterprise security market includes roughly 2,000 vendors! The market is extremely noisy with hype terms like Artificial Intelligence used very freely. When everyone makes the same claims, how can you know who to believe? And when companies stir up F.U.D. about A.I. attackers, it causes everyone to lose faith in what vendors say.
At ExtraHop, we aim to rise above the hype in the cybersecurity market. The live attack simulation is one way that we can do that by running real attacks in our demo environment and allow you to see how that works in the product. Read more about our philosophy of rising above the noise in this blog post from our SVP of Marketing, Bryce Hein.
Discover more