 Blog
Blog
Query. Click. Done.
How to quickly answer questions about suspicious transactions, packet lag, and more with ExtraHop!
Jeena Khan
September 4, 2018
While collecting data is critical, nothing is more powerful than being able to quickly find exactly what you need. In 7.3, the ExtraHop Explore and Trace appliances team up to deliver filtered results for all of your search needs with the push of an (easy) button.
With the Explore appliance you can create complex queries (or simple ones, too) that search for stored flow and L7 transaction records. That means you can filter results for individual transactions that happened between your devices over key network protocols: transactional (such as HTTP, CIFS, and NFS), message-based (such as ActiveMQ, DNS, and DHCP), and session-based (such as SSL and ICA).
Say you've queried for all suspicious HTTP requests by client IP address, and one laptop is noticeably present. You're going to want to check if a compromised client is responding to command and controls servers: the beginning of a potential attack chain.
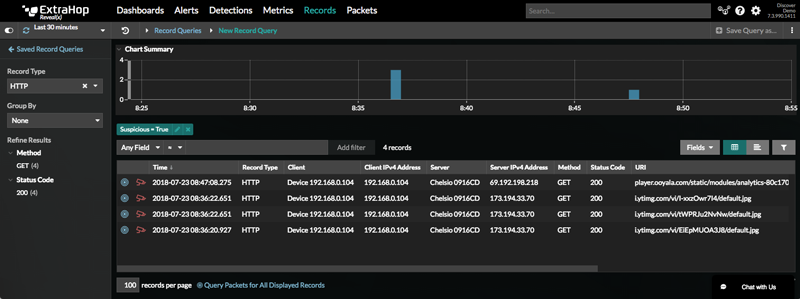
So now you have a pile of worrisome records: what next? To dig deeper, you need the packet payload stored on the Trace appliance.

Voila! With the click of a button, your results are filtered to only the packets you need.
Filtering by records buys you 10x the efficiency in querying for the right transactions that you need payload data for. With a few steps, you can then download the packets, and view them in your favorite packet analyzer, such as Wireshark, and solve whatever crisis threatened the serenity of your network.
Here are some other problems we can help solve:
- Download packets for your VoIP traffic to listen to call playback, and then make sure that the expedited forwarding tag is present. If it isn't, it might be the cause of poor audio quality, because your VoIP packets are lagging behind less time-sensitive traffic.
- Configure session key forwarding and store keys for an efficient way to decrypt traffic you couldn't see before. (You can't search for records or packets if the data is encrypted.)
Discover more